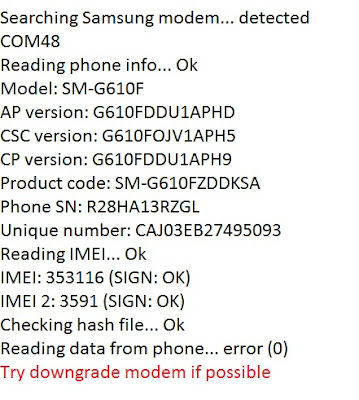
Infinity Chinese Miracle-2 MTK/Mediatek v2.11
New features activated Infinity Chinese Miracle-2 MTK/Mediatek v2.11 - New features activated Read about CM2MT2 v2.10 Infinity Chinese Miracle-2 MTK/Mediatek v2.10 - New MTK chips and UFS storage because v2.10 has major improvements and v2.11 is a successor of v2.10 with new improvements and fixes ! Core BugFix : META protocol updated Changed : Loader v2012 supported and tested Service Changed : Identify in META now read NVRAM dump that is compatible with flash mode writing !*Feature may not work on old devices - Android 4.x, MT6572 and similar legacy chips !*Feature useful also for devices which can not connect via flash mode as security save way Changed : Identify now also verify EXTRA security flags !*Signed types detection ( RSA signed security items ) !*Encrypted types detection ( Vendor-modified security items ) !*Edit/Repair security on those types IS NOT possible at the moment ! !*Swap security on those types IS NOT possible at the moment